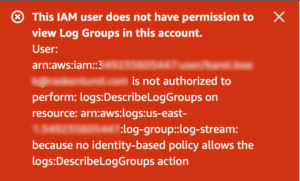
Error:
This IAM user does not have permission to view Log Groups in this account.User: arn:aws:iam::…..:user/….. is not authorized to perform: logs:DescribeLogGroups on resource: arn:aws:logs:us-east-1……log-group::log-stream: because no identity-based policy allows the logs:DescribeLogGroups action
Solution: Create an IAM policy for accessing CloudWatch Logs resources
- Go to IAM dashboard.
- Select Users menu from the left hand side menu.
- Select the user you want to provide the permission.
- Select the permissions tab and click on Add Permissions button.
- Click Create Policy link.
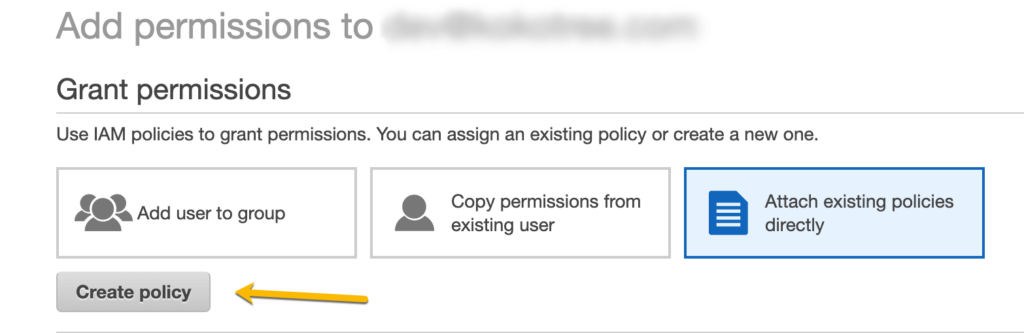
- On Create Policy page, select the following things:
- Select CloudWatch Logs service.
- Ensure that the following permissions are selected: CreateLogGroup, CreateLogStream, DescribeLogStreams, GetLogEvents, PutLogEvents, PutRetentionPolicy, DescribeLogGroups
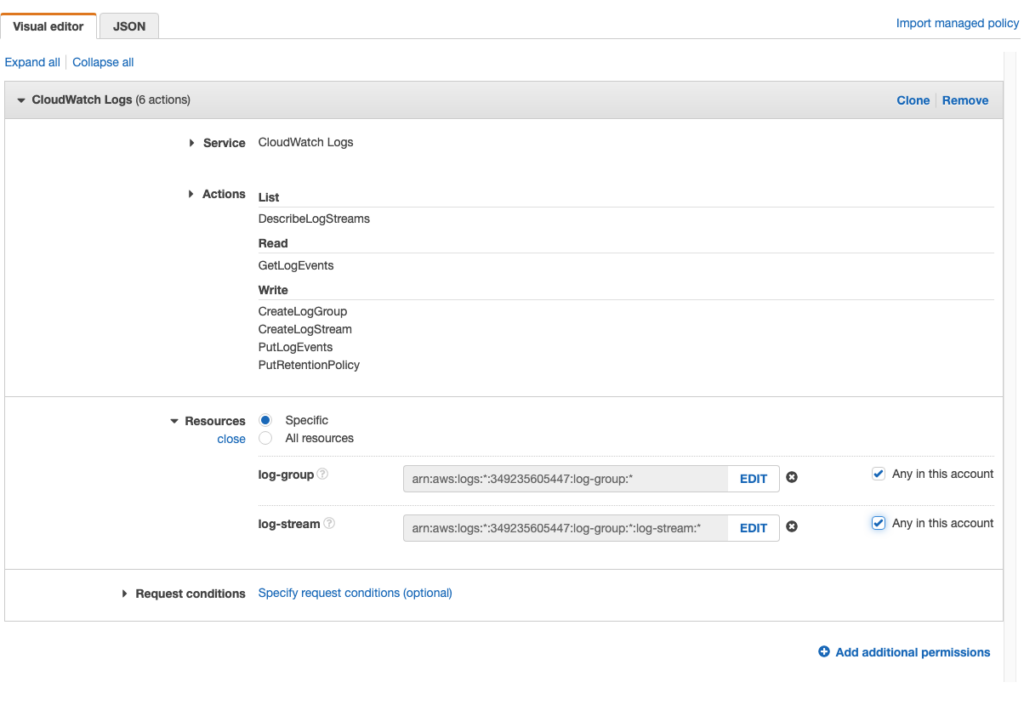
- Click Next, to review poilcy.
- In the name field enter IAMAccessCloudWatchLogsResourcesPolicy.
- Click Create Policy button.
- Next page will give you a success message that the polciy has been created.
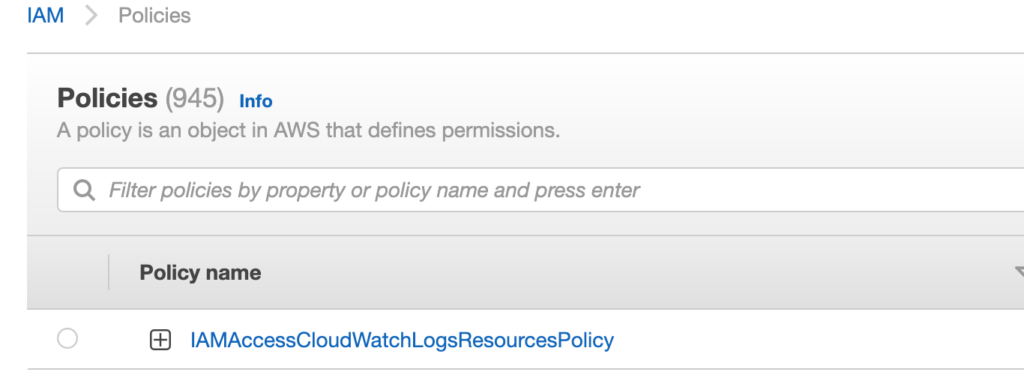
- Go back to the 3rd step (Select the user you want to provide the permission) and click Next: Permissions button .
- In the Set permissions section, click Attach existing policies directly tab.
- Check the IAMAccessCloudWatchLogsResourcesPolicy policy.
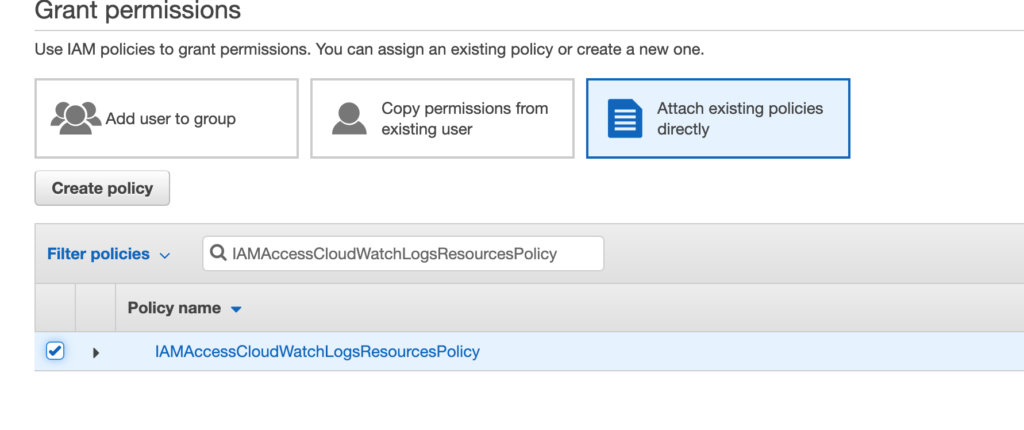
- Click next to attach IAMAccessCloudWatchLogsResourcesPolicy policy to the user.
- The user should be able to access the CloudWatch Logs resources.